Introduction
At Realworld, we are always striving to ensure that sensitive and private data is kept private.
With this in mind, Coen issued a challenge to the Diagnostics team to try and break the Diagnostics Collector.
At stake was the integrity of the collector, but also a fabulous 1kg of Chocolate Eggs as prize to whomever could break into it and retrieve sensitive information.
The Diagnostics team set out to test the security of the Collector. Could they rise to the challenge and beat the Collector?
Preparation
Gert gave the Diagnostics team a head-start with some tips on doing penetration testing (and pictures of his slippers!).

Armed with this knowledge, the team began to prepare in earnest. At first, it was decided that each member would compete with the others for the fabled eggs, but a twist appeared in the challenge.
There would only be one day in which to accomplish this monumental task!
Given this new information, the team decided to collaborate more than compete, and thus the stage was set for an epic confrontation.
Penetration Testing Day
The day of the testing dawned deceptively quiet. However, the team were ready. Meenakshi had provided yet another advantage to the team through her research, and found the software package Kali, ideal for taking on the tough foe that was the Collector.

Network vulnerability scanning was the logical way to start finding weaknesses in the Collector’s defences.
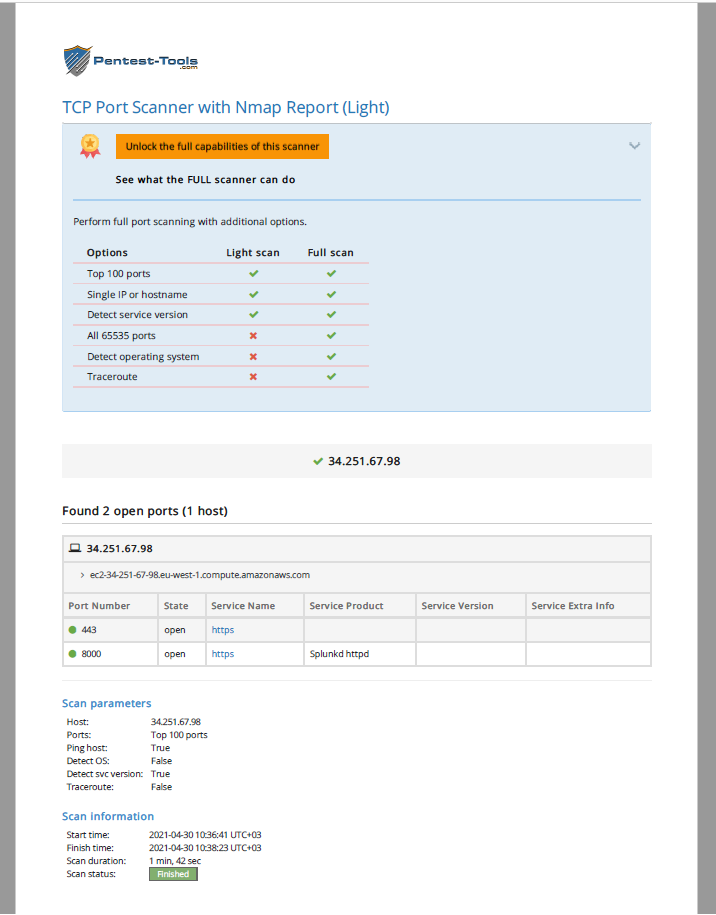
Once the network vulnerability scanning was complete, it was time to bring out the big guns and try to exploit the Collector. Time and again the team’s attacks were turned aside, but they ploughed on, undeterred, trying new attacks. One could be forgiven for thinking that the team attacking from so far apart on the globe would mean that it was easier for the Collector to defend itself, but this was not the case.
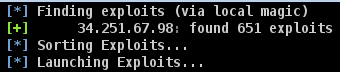
Throughout the day, the team would confer on what was occurring from their respective attacks, and attempt to get past the Collector. They would then shift their focus to better probe the defences. But the day was wearing on.
Was there still time to crack the Collector?
The End of the Day
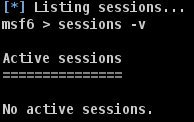
When the smoke cleared from the final attacks by the team, the Collector stood whole and unbroken. In a last meeting for the day, Coen declared the Collector victorious! It had protected its secrets.
No one from the team would be able to lay claim to the Chocolate Eggs.
The data was safe!
Epilogue: Report
In all seriousness, the Diagnostics Team are very proud to say that the Diagnostics Collector is secure.
Penetration Testing failed to retrieve any sensitive information.
TESTERS
Meenakshi Sundareswari
Koen van Keulen
SOFTWARE USED
Several different software penetration tools were used.
Kali – this included a whole suite of different tools (including Nmap, Spike, ZAP and Metasploit below, along with a lot of others).
NMap – to check ports, and for vulnerability checks.
Spike – check vulnerability.
ZAP – check vulnerability.
Metasploit – to try exploits.
REPORT TABLE
| SOFTWARE USED | ATTACK/OTHER | RESULT | CONCLUSION |
| NMap | Check Ports 443, 22, 8000 and Vulnerability scan | Ports Identified – no penetration | Ports are secured/Vulnerability cannot be penetrated |
| Spike | ssl test 443 (vulnerability scan) | No Penetration | Vulnerability cannot be penetrated |
| ZAP | web test 8000 (vulnerability scan) | No Penetration | Vulnerability cannot be penetrated |
| Metasploit | Exploit attacks | No Penetration and no data retrieved | Exploits cannot penetrate the Diagnostics Collector protection, and the data is secure. |

